Thousands of North Korean IT workers have infiltrated the Fortune 500—and they keep getting hired for more jobs
“They are wildly successful,” said Google Threat Intelligence Group expert Michael Barnhart, who has been tracking North Korea and collecting intelligence broadly for decades.

- Fortune 500 companies have unwittingly hired thousands of software engineers who claim to be American developers, but are actually North Korean citizens using stolen or fake identities. Through legitimate employment, the IT workers are illegally funneling their salaries to Kim Jong Un’s regime to fund prohibited weapons of mass destruction and ballistic missile programs. The U.S. Treasury, State Department, and FBI collectively estimate the IT workers scam has generated hundreds of millions each year since 2018.
About 95% of the résumés Harrison Leggio gets in response to job postings for his crypto startup g8keep are from North Korean engineers pretending to be American, the founder estimates. He even once interviewed a job seeker who claimed to have worked at the same Manhattan-based cryptocurrency exchange as him, during the time he worked there.
Turns out, it was all a ruse: The programming languages the engineer said the company used was incorrect, and he claimed to have floated among teams rather than embedding in a single group, which “wasn’t a thing there,” said Leggio.
Nowadays, Leggio told Fortune he won’t even set up an interview with a candidate who seems promising on paper unless they agree to one final step.
“Say something negative about Kim Jong Un,” Leggio tells potential job candidates, referring to the third-generation authoritarian Supreme Leader of North Korea, officially the Democratic People’s Republic of Korea (DPRK). Through research, Leggio learned insulting the DPRK’s Supreme Leader is forbidden, and North Korean citizens could face serious punishments for showing anything less than reverence.
“The first time I ever did it, the person started freaking out and cursing,” said Leggio.
The job seeker subsequently blocked Leggio across all social-media platforms; now, Leggio makes the same request before every single interview. Other startups and founders he knows are asking the same thing of job seekers, he said.
A yacht versus a missile
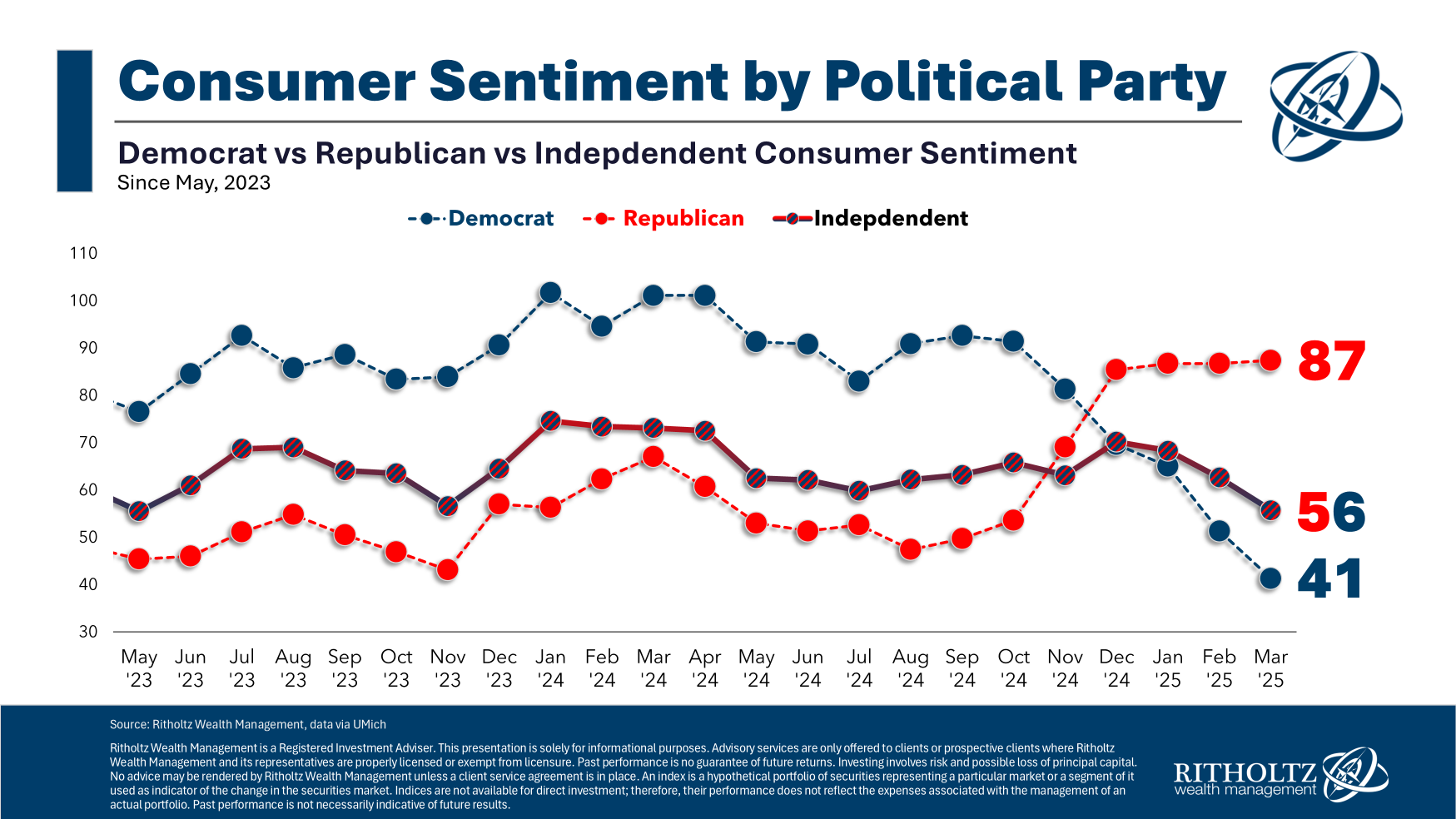
The UN estimated the North Korean IT worker scam has generated $250 million to $600 million every year since 2018. As a result, cybersecurity experts of all stripes have banded together to share information about the strategies, profiles, VPNs, and signs to watch for. But AI has emboldened the North Korean scheme, allowing the IT workers to develop scripts so they can hold down as many as six or seven jobs at a time, disguise their appearance, and even alter their voices so they don’t have an accent—or so they sound like a woman instead of a man. Experts predict the scope and scale will expand in 2025, moving across Europe and Asia with well-honed social engineering tactics paired with more aggressive job hunting at European defense and government companies.
Michael Barnhart, an intelligence leader at Google Cloud who has been tracking North Korean threats for years, explained the scheme this way: North Korean engineers, deployed to locations in China and Russia, use AI to create bios with eye-catching company experience highlighted. They work in teams to apply for jobs en masse, using stolen American identities, or with the help of facilitators in the U.S. or abroad. Some IT workers have even created front companies to pose as legitimate recruiting firms or web-design agencies, for instance, that larger Fortune 500 companies then hire—not realizing it’s a North Korean front, said Barnhart.
“Right now, we have North Korean IT workers adapting so much that they’re not even doing IT work anymore,” he told Fortune.
Among global companies, security teams have implemented different systems and strategies for rooting out North Korean IT workers seeking jobs as well as those already employed and working at companies, Barnhart said. And the stakes couldn’t be higher. The FBI reported the money funds nuclear weapons and operations, and the intelligence and data the IT workers illegally pilfer from companies is directed toward extortion, espionage, and data theft.
“There are criminals who steal your money to get yachts, but in this case, your money isn’t going to a Lamborghini—it’s going back to fund nuclear munitions,” said Barnhart. “A yacht versus a missile—attribution matters.”
300+ incidents in 2024
Bojan Simic, CEO of identity-verification firm Hypr, built a product specifically for companies to verify people's identities because of the North Korean threat, he told Fortune. As a tech founder, he also deals with the issue within his own company. Simic accidentally hired an engineer who did a great job during the interview, but then the person who showed up to be onboarded on their first day wasn’t the person he hired. The engineer also failed a geolocation check, Simic said, and appeared to be in Spain when he claimed to live in Poland.
Emi Chiba, a senior principal analyst at Gartner who has been researching the issue, told Fortune security experts should partner with internal human-resources teams to periodically re-verify the identities of employees and strengthen recruiting practices. The goal is to ensure job candidates aren’t hiding their locations overseas and pretending to be based in the U.S. Those practices range from camera-on video interviews to using identity verification tools with geolocation features to compare a government ID with a selfie, which would help match people to their identities and locations, she said.
“One of the biggest things you can do to combat this is training up HR staff,” added Barnhart.
Despite the efforts to disrupt them, cybersecurity firm CrowdStrike reported North Korean IT workers, a group it calls Famous Chollima, were behind 304 incidents in 2024—and its activities ramped up during the latter half of the year. In its latest assessment, CrowdStrike predicted Famous Chollima will continue its campaigns in 2025 given the financial success it’s seen and limited impact from federal prosecutions and government indictments last year.
Adam Meyers, senior vice president of CrowdStrike’s counter adversary team, told Fortune Famous Chollima has two main tentacles. One is a malware operation that focuses on intelligence collection and crypto theft, like the $1.5 billion cryptocurrency heist from a Dubai exchange. The other is the IT workers scam in which North Korean engineers get legitimate jobs and remit their salaries to North Korea to fund nuclear weapons, operations, and trade. The two prongs also work together to share intelligence.
In the IT worker scheme, once someone involved gets an interview, North Koreans use remote-desktop tools to help coach people through the Q&A with a recruiter.
Aidan Raney, founder of Farnsworth Intelligence, posed as an American willing to help North Koreans to investigate the issue for a client who almost hired a fake engineer. During the course of two video calls with three or four people who all said their names were “Ben,” Raney learned the details. “The Bens” would handle all the upfront work for him—creating a fake LinkedIn profile to verify his new identity for U.S. recruiters, formulating a bio, and sending it out to dozens of job postings with a new Gmail address they set up.
The Bens even modified Raney’s headshot to a black-and-white photo so it wouldn’t resemble his usual picture, Raney told Fortune. If Raney got a job, he would show up for meetings, like a morning stand-up or scrum, and go about his day while a North Korean engineer handled the workload. He would be allowed to keep 30% of the salary, but had to transfer 70% to the Bens using crypto, Paypal, or Payoneer.
“What they were trying to do was use my identity to bypass background checks and so they wanted this fake persona they created to be extremely close to the real-life version,” said Raney.
The Bens got Raney an interview, and while it was ongoing, they used a remote-desktop application to set up a notepad on Raney’s screen so they could write out responses to the questions from the interviewer, Raney explained. And it worked: Raney got a verbal offer for a job with a private government contractor that paid $80,000 a year.
He then had to immediately turn around and tell the company he couldn’t accept the offer and apologize for claiming their time.
“Now that they’re using real Americans who have verified identities and documents and they’re using their real faces—everything looks real,” said Raney. “There would be nothing stopping them from being hired.”
In the past two years, the Department of Justice has indicted dozens of North Korean citizens and unnamed co-conspirators in the scheme, charging them for stealing American identities, conspiracy to violate U.S. sanctions, wire fraud, and money laundering. The FBI’s cybercrime wanted list includes at least 14 North Korean IT workers sought by authorities, and the State Department announced a reward of up to $5 million for information on those involved.
Relatedly, a Nashville man was arrested and an Arizona woman pleaded guilty for running “laptop farms” as part of the scheme. The laptop-farm keepers work with the North Korean gangs to keep laptops shipped from various U.S. companies at their homes for a monthly fee, in exchange for accepting the devices and installing remote-desktop software so the IT workers can work outside the U.S., authorities alleged.
In the Arizona case, a 49-year-old woman outside Phoenix helped North Korean co-conspirators get jobs at Fortune 500 banks, a television network, aerospace manufacturer, car manufacturer, and a Silicon Valley tech company, court documents show. Using 60 stolen identities, she helped the IT workers get jobs at 300 companies that paid them millions for their work.
“That a woman living her quiet life in the outskirts of Phoenix can allegedly get so entangled in something like this clearly indicates our adversaries are getting more sophisticated and stealthier, so it’s critical that businesses and citizens be hyper-vigilant with their cyber activities,” said FBI Special Agent Akil Davis of the Phoenix Field Office last year.
Ultimately, companies have to do more than just shipping a laptop out to a remote worker, said Chiba of Gartner.
“It reminds me of trying to get into a club—the bouncer is looking between you and your ID to see if it’s you and if it has the right photo,” Chiba said. “If the ID is checked once and only that once and that is the only mitigation tactic, it’s probably not enough to catch someone.”
In a statement, Payoneer told Fortune it proactively works to combat fraud and financial crime on its platform through robust compliance systems and that it works closely with both regulators and law enforcement.
This story was originally featured on Fortune.com