Cork Protocol hacked for $12M, smart contracts paused
Cork Protocol, a decentralized finance (DeFi) platform, was hit by a smart contract exploit on May 28, resulting in the loss of roughly $12 million in digital assets.Cybersecurity firm Cyvers said the hack occurred at 11:23:19 UTC and was funded by an address ending in “762B.” According to the firm, the attacker used the exploit to steal roughly 3,761 Wrapped Staked Ether (wstETH), which was converted to Ether (ETH) almost immediately after the attack.“We are investigating a potential exploit on Cork Protocol and are pausing all contracts. We will report back with more information,” Cork Protocol co-founder Phil Fogel wrote on X.Cork Protocol smart contract exploit details. Source: CyversThe Cork Protocol exploit is the latest hacking incident to impact the crypto industry as cybersecurity continues to be a major issue in the sector, lowering consumer confidence, and prompting calls to improve security measures from crypto industry executives.Related: Hacken CEO sees ‘no shift’ in crypto security as April hacks hit $357MCetus hacked for $223 million days agoThe Cetus decentralized crypto exchange (DEX), a trading platform built on the Sui network, was hacked on May 22, resulting in $223 million in stolen funds.Sui validators froze a majority of the funds, sparking a debate about the centralization of the network and the appropriate course of action for blockchain validators following a major hacking incident.The Cetus team announced a $6 million bounty for white hat hackers assisting in the return of the remaining stolen funds. Blockchain security firm Dedaub released a post-mortem report dissecting the incident details. According to the report, the hack was caused by an exploit of the liquidity parameters used by the Cetus automated market maker (AMM).The hackers manipulated the field by altering values that went undetected in a most significant bits (MSB) check. Changes to a binary code’s most significant bits dramatically alter the values produced by that binary code.This allowed the hackers to add massive amounts of liquidity to the system with only a keystroke and drain other liquidity pools of hundreds of millions of dollars.Magazine: Weird ‘null address’ iVest hack, millions of PCs still vulnerable to ‘Sinkclose’ malware: Crypto-Sec



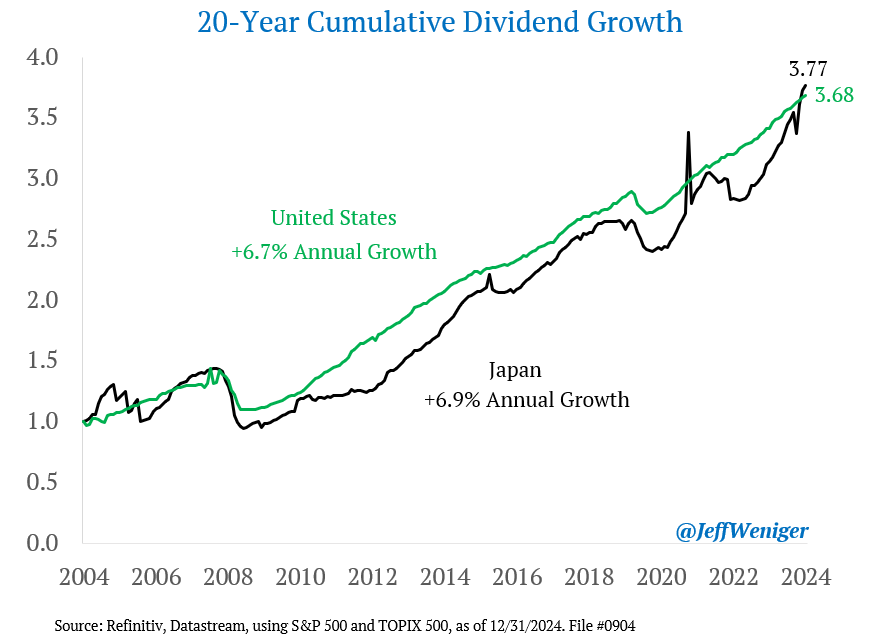
Cork Protocol, a decentralized finance (DeFi) platform, was hit by a smart contract exploit on May 28, resulting in the loss of roughly $12 million in digital assets.
Cybersecurity firm Cyvers said the hack occurred at 11:23:19 UTC and was funded by an address ending in “762B.” According to the firm, the attacker used the exploit to steal roughly 3,761 Wrapped Staked Ether (wstETH), which was converted to Ether (ETH) almost immediately after the attack.
“We are investigating a potential exploit on Cork Protocol and are pausing all contracts. We will report back with more information,” Cork Protocol co-founder Phil Fogel wrote on X.
The Cork Protocol exploit is the latest hacking incident to impact the crypto industry as cybersecurity continues to be a major issue in the sector, lowering consumer confidence, and prompting calls to improve security measures from crypto industry executives.
Related: Hacken CEO sees ‘no shift’ in crypto security as April hacks hit $357M
Cetus hacked for $223 million days ago
The Cetus decentralized crypto exchange (DEX), a trading platform built on the Sui network, was hacked on May 22, resulting in $223 million in stolen funds.
Sui validators froze a majority of the funds, sparking a debate about the centralization of the network and the appropriate course of action for blockchain validators following a major hacking incident.
The Cetus team announced a $6 million bounty for white hat hackers assisting in the return of the remaining stolen funds.
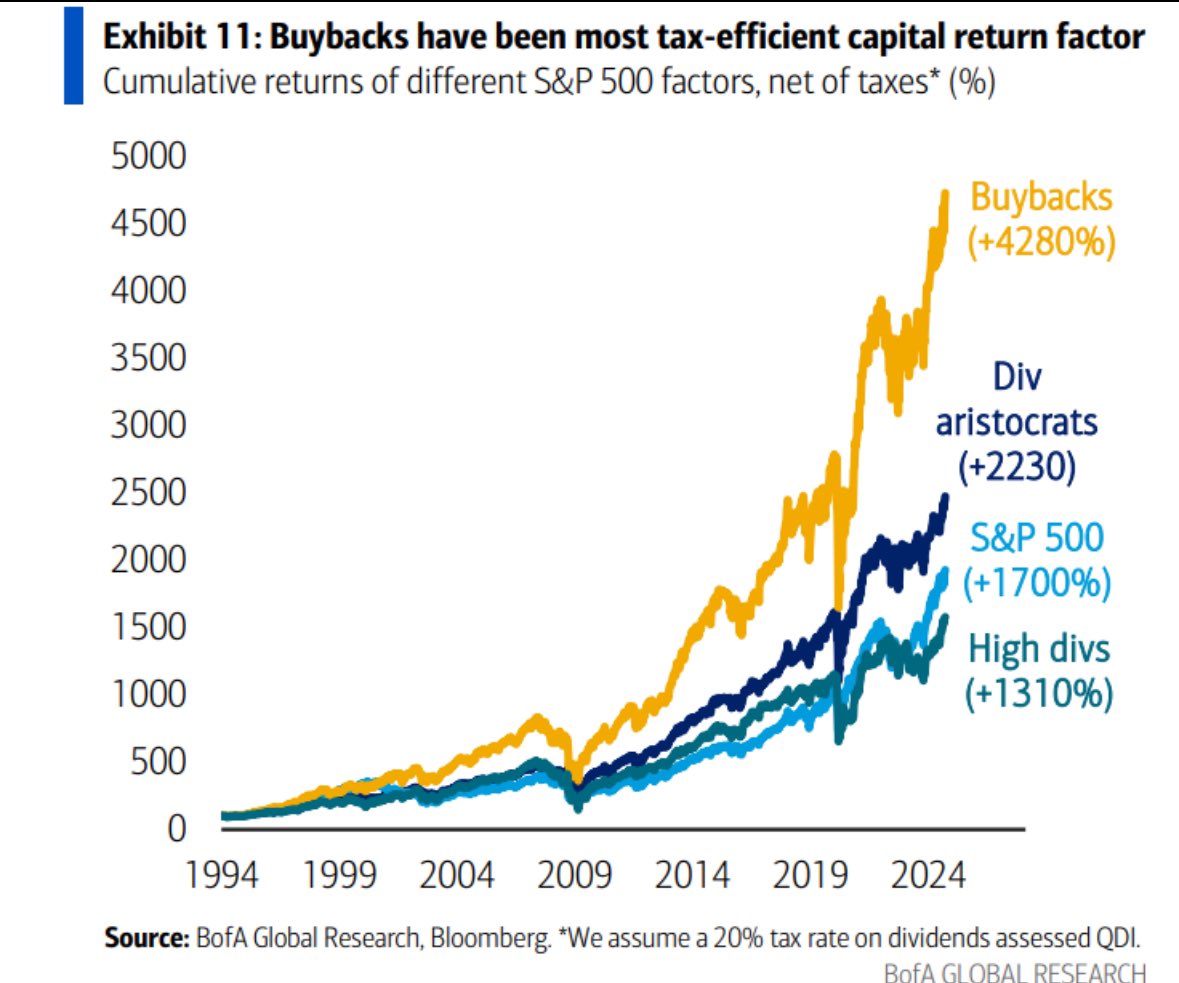
Blockchain security firm Dedaub released a post-mortem report dissecting the incident details. According to the report, the hack was caused by an exploit of the liquidity parameters used by the Cetus automated market maker (AMM).
The hackers manipulated the field by altering values that went undetected in a most significant bits (MSB) check. Changes to a binary code’s most significant bits dramatically alter the values produced by that binary code.
This allowed the hackers to add massive amounts of liquidity to the system with only a keystroke and drain other liquidity pools of hundreds of millions of dollars.
Magazine: Weird ‘null address’ iVest hack, millions of PCs still vulnerable to ‘Sinkclose’ malware: Crypto-Sec